Los investigadores de ciberseguridad han señalado múltiples campañas de exploits que aprovecharon fallas ahora parcheadas en los navegadores Apple Safari… 🔒 Este contenido es exclusivo para miembros registrados. 👉 Inicia sesión o regístrate gratis para leerlo completo.
Blog
Los ciberdelincuentes se aprovechan de las búsquedas de software más populares para propagar el malware FakeBat
Investigadores de ciberseguridad han descubierto un aumento en las infecciones de malware derivadas de campañas de publicidad maliciosa que distribuyen… 🔒 Este contenido es exclusivo para miembros registrados. 👉 Inicia sesión o regístrate gratis para leerlo completo.
CrowdStrike revela la causa raíz de las interrupciones del sistema global
La empresa de ciberseguridad CrowdStrike ha publicado su análisis de la causa raíz que detalla el fallo de la actualización del software… 🔒 Este contenido es exclusivo para miembros registrados. 👉 Inicia sesión o regístrate gratis para leerlo completo.
‘Stargazer Goblin’ crea 3.000 cuentas falsas de GitHub para la propagación de malware
Un actor de amenazas conocido como Stargazer Goblin ha creado una red de cuentas de GitHub no auténticas para alimentar… 🔒 Este contenido es exclusivo para miembros registrados. 👉 Inicia sesión o regístrate gratis para leerlo completo.
Explotan la falla de la aplicación Telegram para propagar malware oculto en videos
Una falla de seguridad de día cero en la aplicación móvil de Telegram para Android llamada EvilVideo hizo posible que… 🔒 Este contenido es exclusivo para miembros registrados. 👉 Inicia sesión o regístrate gratis para leerlo completo.
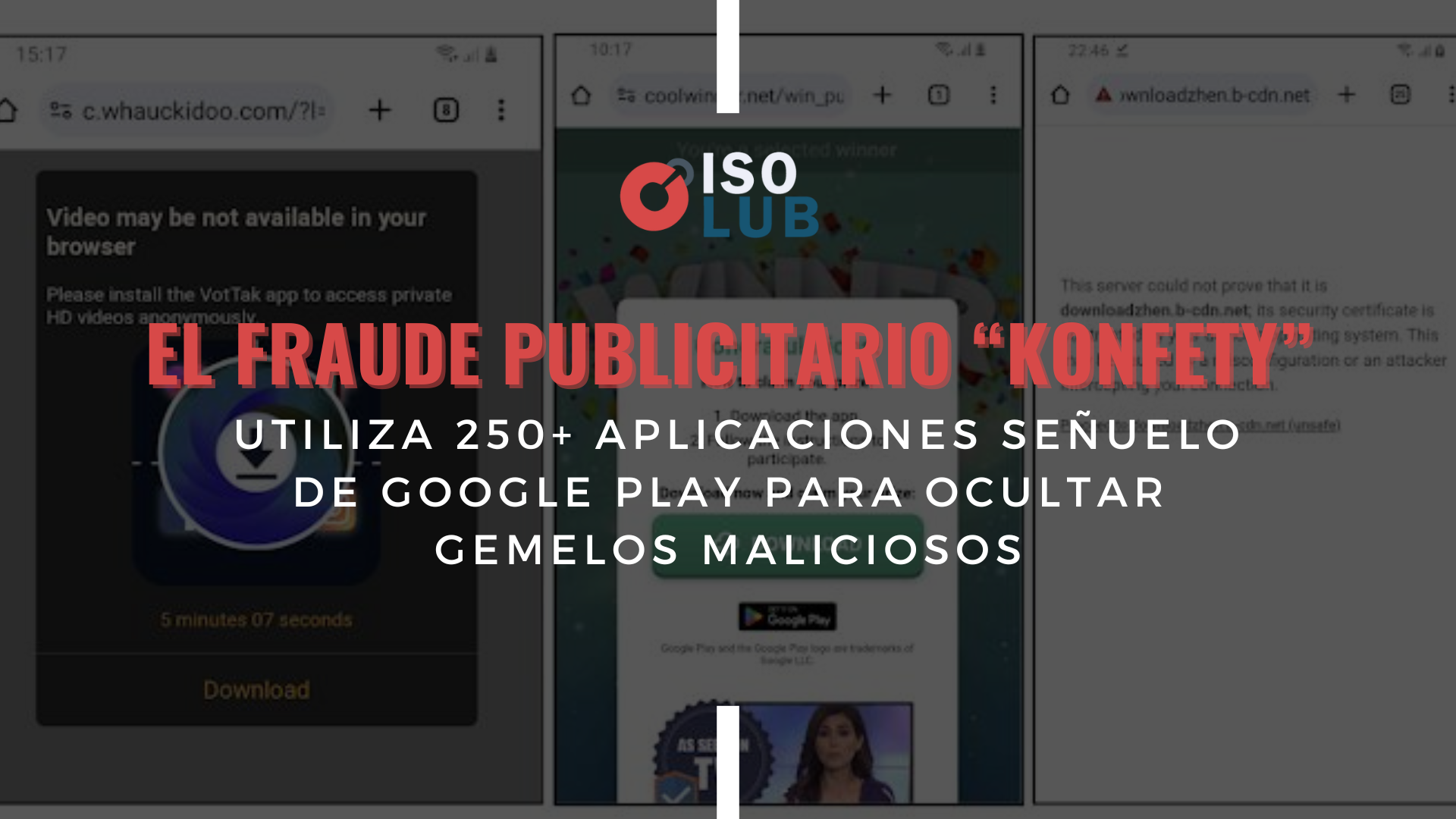
El fraude publicitario ‘Konfety’ utiliza 250+ aplicaciones señuelo de Google Play para ocultar gemelos maliciosos
Han surgido detalles sobre una “operación masiva de fraude publicitario” que aprovecha cientos de aplicaciones en Google Play Store para… 🔒 Este contenido es exclusivo para miembros registrados. 👉 Inicia sesión o regístrate gratis para leerlo completo.
Repatriación de la Nube: ¿Por qué algunas Empresas están Abandonando AWS, Azure y Google Cloud?
La llegada de Amazon Web Services (AWS) y, más tarde, de alternativas como Azure y Google Cloud, fue vista como… 🔒 Este contenido es exclusivo para miembros registrados. 👉 Inicia sesión o regístrate gratis para leerlo completo.
Una nueva vulnerabilidad de OpenSSH podría llevar a RCE como root en sistemas Linux
Los mantenedores de OpenSSH han lanzado actualizaciones de seguridad para contener una falla de seguridad crítica que podría resultar en… 🔒 Este contenido es exclusivo para miembros registrados. 👉 Inicia sesión o regístrate gratis para leerlo completo.
EE.UU. prohíbe el software de Kaspersky, citando riesgos para la seguridad nacional
La Oficina de Industria y Seguridad (BIS, por sus siglas en inglés) del Departamento de Comercio de Estados Unidos anunció… 🔒 Este contenido es exclusivo para miembros registrados. 👉 Inicia sesión o regístrate gratis para leerlo completo.
More_eggs malware disfrazado de currículum se dirige a los reclutadores en un ataque de phishing
Los investigadores de ciberseguridad han detectado un ataque de phishing que distribuye el malware More_eggs haciéndose pasar por un currículum,… 🔒 Este contenido es exclusivo para miembros registrados. 👉 Inicia sesión o regístrate gratis para leerlo completo.